In today’s digital age, ensuring the security and privacy of online communications is more critical than ever. One of the most trusted tools for this purpose is PGP (Pretty Good Privacy), a data encryption and decryption program designed to provide cryptographic privacy and authentication. At the core of PGP’s functionality is the “Web of Trust” principle, a decentralized trust model that enables users to securely communicate without relying on central authorities. This article explores how the Web of Trust works and how it powers PGP to protect data.
1. What is PGP?
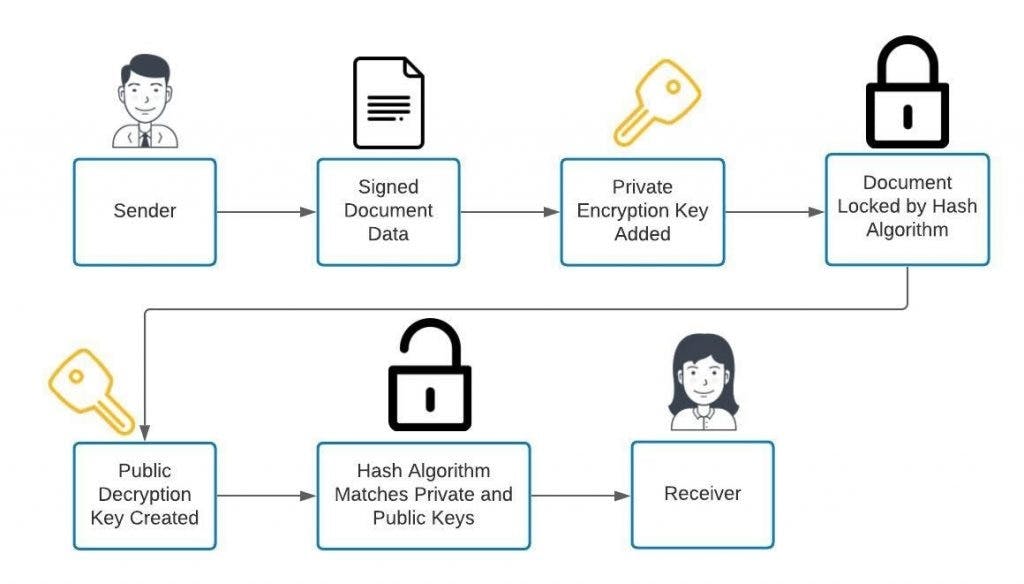
PGP is an encryption system first developed by Phil Zimmermann in 1991 to secure online communications. It allows users to encrypt emails, files, and even digital signatures, ensuring that only the intended recipient can decrypt and read the message.
- Encryption: PGP uses a hybrid cryptographic approach, combining symmetric-key encryption (faster for encrypting the actual data) with asymmetric-key encryption (for secure exchange of keys).
- Authentication: PGP ensures that messages are not only encrypted but also authenticated, so the recipient can verify the sender’s identity.
PGP relies heavily on the public-key cryptography model, where each user has a pair of keys: a public key (shared with others) and a private key (kept secret). When someone wants to send you a secure message, they use your public key to encrypt it, and only your private key can decrypt it.
2. The “Web of Trust” Explained
Unlike traditional models that rely on centralized certificate authorities (CAs) to verify identities (as in SSL/TLS certificates), PGP uses a decentralized system known as the Web of Trust (WoT). In this model, trust is built through personal relationships and mutual verification between individuals.
The Web of Trust operates on a peer-to-peer basis, meaning users validate each other’s identities directly. When a user trusts another’s public key, they can sign that key as a mark of trust. This system allows users to build networks of trust without requiring a central entity to vouch for the authenticity of public keys.
Key Concepts of the Web of Trust:
- Trust Chains: In the Web of Trust, trust is established through chains. For example, if Alice trusts Bob’s public key, and Bob trusts Carol’s, Alice might trust Carol’s public key indirectly, depending on the strength of the trust relationships.
- Key Signing: Users can digitally “sign” other users’ public keys, signifying they trust that the key truly belongs to the claimed person. The more signatures a key has, the more trust it accumulates.
- Levels of Trust: PGP allows users to assign different levels of trust to public keys:
- Full trust: The key is fully trusted, meaning the user trusts both the key and the keyholder’s ability to validate others.
- Marginal trust: The user trusts the key, but perhaps not fully the keyholder’s ability to vouch for others.
- No trust: The key is not trusted, and the user does not rely on it for secure communication.
3. How Does the Web of Trust Work?
When a user creates a PGP key pair (public and private keys), they publish their public key on key servers or share it with others directly. To build trust, users can ask others to verify and sign their public keys. This verification can be done through personal interactions (like meeting in person and verifying identities) or other trusted channels.
Here’s a breakdown of the process:
- Key Generation: Each user generates their own public/private key pair.
- Key Sharing: Users share their public keys with others. This can be done via email, publishing on key servers, or face-to-face exchanges.
- Key Signing: Users sign each other’s public keys after verifying the key’s authenticity, creating a signature that attests to their trust.
- Web of Trust Growth: As more people sign and trust each other’s keys, a web of trust forms, allowing users to trust the keys of others they may not know directly, based on mutual trust connections.
For example:
- Alice signs Bob’s public key because she knows him personally.
- Bob signs Carol’s key because he trusts her.
- Alice may now choose to trust Carol’s key because of her trust in Bob, creating an indirect trust relationship.
4. Advantages of the Web of Trust
The Web of Trust has several advantages over centralized models like Certificate Authorities (CAs):
- Decentralization: There’s no need for a central authority to manage trust relationships, making it resilient and adaptable.
- Community-based Trust: Trust is built within communities of users who know each other, reducing reliance on a single point of failure or corruption (as can happen with compromised CAs).
- Scalability: As more users join and sign keys, the Web of Trust grows organically, covering a wide range of users and use cases.
5. Challenges of the Web of Trust
While the Web of Trust offers many benefits, it also presents some challenges:
- Manual Key Signing: The process of verifying identities and signing keys is often manual and can be inconvenient, especially for users who do not meet in person.
- Trust Management: Deciding who to trust and at what level can be complex, particularly when dealing with indirect trust relationships.
- Scalability Limitations: In larger networks, it can be difficult for users to determine whether to trust a distant key based on multiple levels of indirect trust.
6. Real-World Use of PGP and the Web of Trust
PGP and the Web of Trust are widely used in various fields:
- Email Encryption: PGP remains a popular tool for email encryption, especially among privacy-conscious users and organizations like journalists, activists, and cybersecurity professionals.
- Software Distribution: Developers often use PGP to sign software packages, ensuring users can verify the authenticity and integrity of downloads.
- Blockchain and Cryptocurrencies: The Web of Trust model has inspired decentralized trust frameworks in blockchain technologies, where peer-to-peer verification plays a crucial role.
7. The Future of Web of Trust
Although PGP remains an essential tool for secure communication, the Web of Trust faces competition from other trust models, such as blockchain-based identity systems and Web of Trust 2.0 efforts. However, its decentralized nature continues to appeal to those who value privacy and community-driven security models.
The Strength of Peer-Based Trust
The Web of Trust is a powerful model for securing communications without relying on centralized authorities. By empowering individuals to vouch for each other, it creates a decentralized and flexible trust network that has stood the test of time. While not without its challenges, the principles behind the Web of Trust continue to inspire innovations in cryptography, blockchain, and decentralized identity systems. Whether you’re encrypting emails or securing software, the Web of Trust remains a cornerstone of modern digital privacy.